Hundreds of open ports and vulnerabilities
One of the areas our software Teem Ops does is regularly scan AWS accounts for over 200 types of potential security issues. These range from insecure ports, open public access, publicly accessible files, administrator access and a range of other areas which can cause headaches to security teams.
So who’s responsibility is cloud security? Don’t AWS provide customer’s with a secure environment?
With cloud comes responsibility.
AWS are very clear on their website that what they offer is full control of your own Infrastructure in a cloud based environment.
This diagram clearly articulates the separation of responsibilities for services such as IaaS, PaaS and other services.
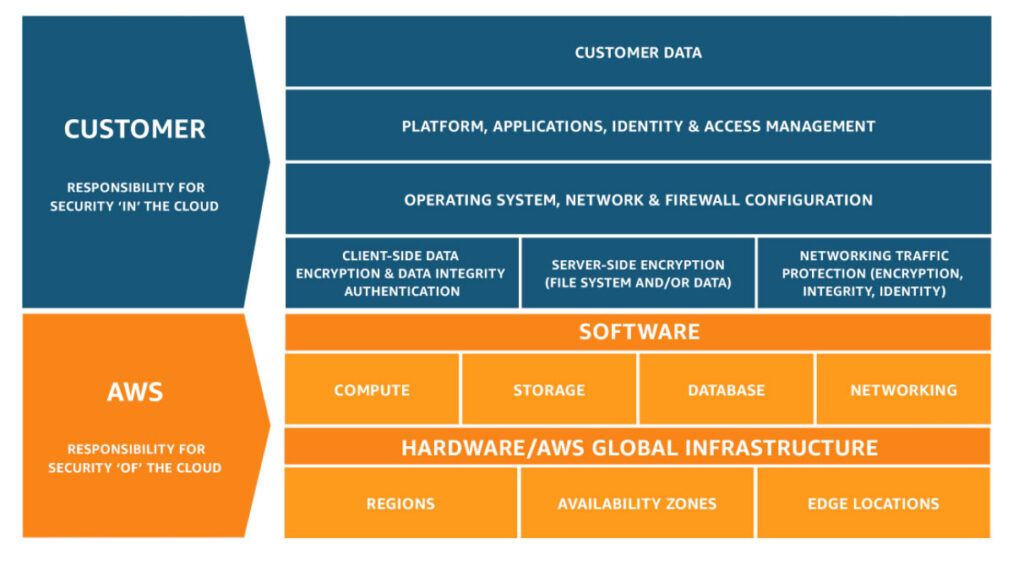
What this indicates is that AWS have a responsibility and you as a customer have a responsibility.
Depending on the type of service you use in AWS will determine the level of responsibility for security. AWS provide a number of tools and controls for security configuration.
To help customers take advantage of AWS security we recommend doing these things
- A complete audit of your current environment.
- Immediately apply the changes identified as being critical and high/
- A planned approach to improving security
- A well articulated security policy and framework for employees and 3rd parties.
So what are some of the most common issues in AWS that are caused by security misconfiguration?
- IAM Users and Roles with Administrator or Over privileged access. For example giving access to anyone to shutdown and terminate all EC2 Instances and RDS databases or delete S3 bucket objects is common.
- Security Groups that provide full access to all ports and all public IP addresses. This can cause someone to gain unauthorized access to a server or database.
- S3 buckets that are public, causing anyone on the Internet to access confidential customer data or company documents.
- Long lived credentials. These can sit on devices such as laptops and cause anyone with access to compromise an AWS account.
These can be easily highlighted in your AWS account with a scan using Teem Ops security auditing tool or services.
